
Product
Be ahead of hackers and Pen-test your cyber security
ICT Group pen-tests both IT and OT networks and applications
After the test, you will receive a very detailed and complete report in which we describe all the vulnerabilities and give advice on how you can structurally improve your cyber security.
How exactly does Pen-testing work?
A pen-test is more than an automated programme that mainly investigates known vulnerabilities. Our ethical hackers use a creative test programme to intelligently deviate from the known patterns in order to discover unpredictable, potential paths. This provides the added value you need. Pen-testing provides you with in-depth insight into the real risks and the options that will increase your security level. We can use multiple entries to examine your systems in various ways.
On the IT side we focus on:
- Company network. The security level of your internal and external (WI-FI) networks.
- (Web) applications. Websites, financial systems, portals and other applications often provide unnoticed access to data and infrastructures. The Pen-test exposes the vulnerabilities.
- Mobile apps and APIs. Mobile apps produce and often transfer a lot of sensitive data and are connected to other (web) services and APIs. We examine all potential risk factors and vulnerable links for a cyber attack.
On the OT side we focus on:
- IACS and OT. The cyber security of Industrial Automation & Control Systems, OT environments, communication systems, gateways and firewalls. Here we use a clearly different approach than within an IT environment. After all, a scan of the network could potentially cause a crash of IACS systems.
- IoT and other hardware. IoT devices and hardware are becoming ever smarter and are often becoming the gateway to systems and data. The Pen-test physically examines the hardware and all software and network options.
We specialise in cyber security for Industrial Automation and Control Systems (IACS). Because OT and IT are becoming increasingly intertwined and the vulnerabilities within the OT domain are increasing, our knowledge of both environments is essential for a complete approach to your cyber security. Combined with our expertise within the domains of industrial automation and critical infrastructure, this makes us the distinctive partner for every cyber security issue.
What sets us apart
We deliver proven solutions, high-quality (certified) services and dedicated professionals who immerse themselves in your market and organisation. This makes ICT Group into the ideal partner for future-proof solutions and long-term cooperation.
Don't wait and be ahead of hackers
The risk of a hack is increasing by the day. When you engage us for a pen-test, you are taking a first important step towards controlled cyber security. We operate with the utmost care so that you have a full understanding of the potential threats and vulnerabilities in your IT and OT environments. Pen-testing lets you know exactly where you stand and what measures are required in the short and long term. What’s more, the cost of pen-testing is a mere fraction of the recovery costs of a cyber incident or the ransom demanded for software and systems that were taken hostage.
I would like an appointment about Pen-testing
- Direct insight into your current cyber security
- Laying the foundation for structural security measures
- IT and OT knowledge combined with 40 years of domain expertise
IT or OT?
In industrial environments, pen-testing of IT and OT environments is equally important. Why? On average, industrial IT environments contain less risky data and the systems are less critical to business operations, so the risks seem lower. On the other hand, hackers have more experience in penetrating IT environments and once inside, IT environments often offer easy access to OT environments. Combined with the growing number of vulnerabilities within OT environments, the risk of hackers actually being able to exploit them increases. This makes the IT environment into a risk factor for OT that should not be underestimated.
Cyber security requires a thorough approach. Pen-testing is an important part of our programme and is based on prevention, detection, reaction and continuous adjustments.
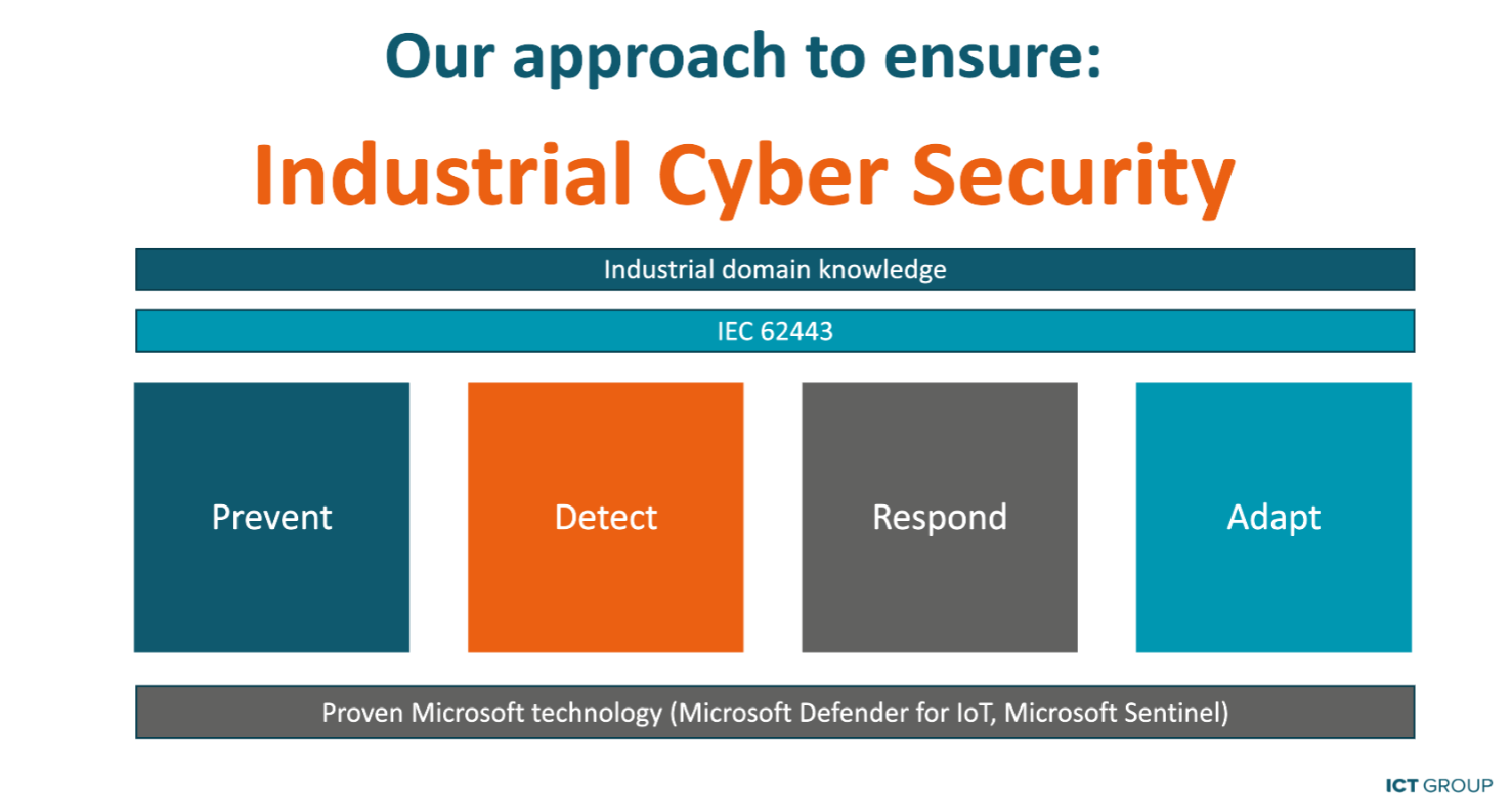
Combine Pen-testing with the Defender for IoT Monitoring Service
Pen-testing exposes the vulnerabilities of your cyber security in a realistic way. Our Defender for IoT Monitoring Service is the logical next step. You have access to fully fledged monitoring tools, reports and proactive cyber security management in order to continuously build on a higher level of security. We know your domain so we can zoom in directly on your needs. Our approach involves the IEC 62443 cyber security standards for industrial automation, thus assuring you of the highest possible security appropriate to your business environment. Would you like to know exactly how it works? Make an appointment for the full story.
