
Product
Manage your cyber security permanently with the Defender for IoT Monitoring Service
Real-time monitoring of network traffic within your OT environment
Monitoring system for your safety position
Knowing the exact current status of your security is in fact no more than a snapshot in time. Tomorrow it will already be different and your security position will have become more vulnerable without you noticing. This is why permanent monitoring of network traffic, combined with updates on your OT environment, are of crucial importance for your cyber security and business continuity.
The Defender for IoT Monitoring Service allows you to get it right the first time and provides you with certainty in the short and long term. We perform a thorough intake from our own Security Operations Centre (SOC) and install software sensors that read the network traffic within your OT environment in real time. We analyse this information and if any deviations are detected that could be a sign of threatening activity, you will immediately receive an alert. You can then take the appropriate measures yourself. The advantages of Defender for IoT Monitoring Service are an adequate response to all your security issues:
- Real-time visibility of the safety status of your OT environment
- Clear analyses and reports and directly applicable advice
- Adequate measures against threats that are taken in time
- Security Operations Centre for targeted actions
- Benefit from proven Microsoft Defender for IoT technology
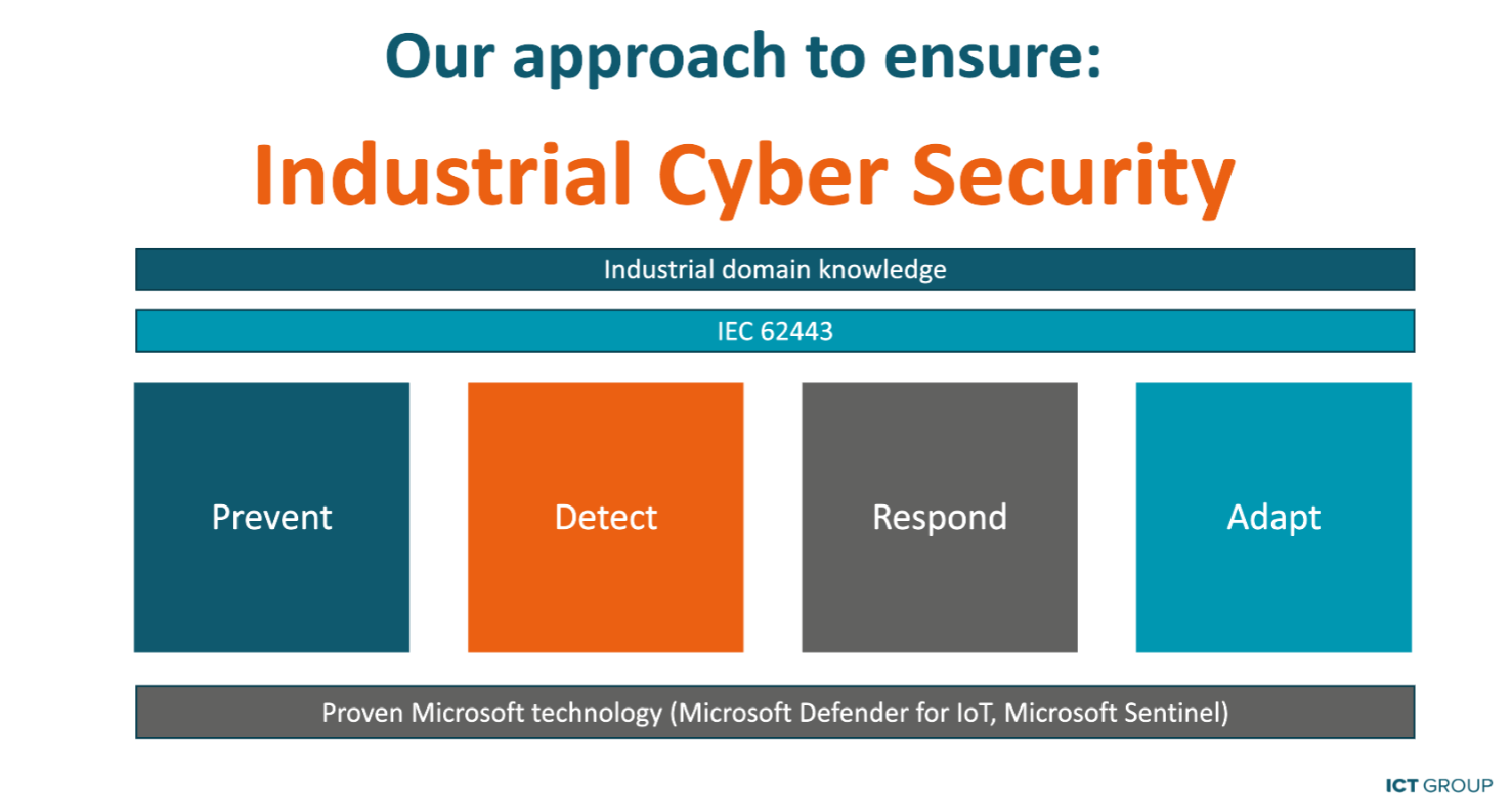
Cyber security requires a thorough approach. We offer this approach with our complete programme for scanning, monitoring and security.
Cyber security as a standard component of your business operations
Cyber security is no longer a peripheral activity. The risks are too great. And we already have the professional services and proven technologies to keep your security at the required level. So what are you waiting for? We know your domain and the area in which you operate, so we can zoom in directly on your needs. Our approach involves the IEC 62443 cyber security standards for industrial automation, thus assuring you of the highest possible security appropriate to your business environment. Would you like to know exactly how it works? Ask for our demo.
What sets us apart
We deliver proven solutions, high-quality (certified) services and dedicated professionals who immerse themselves in your market and organisation. This makes ICT Group into the ideal partner for future-proof solutions and long-term cooperation.
DEMO Defender for IoT Monitoring Service
Combine the Defender for IoT Scan and the Defender for IoT Monitoring Service
The Defender for IoT Scan provides you with a one-off insight into the current security of your OT environment and the cyber security risks you face. The Defender for IoT Monitoring Service is the logical next step. You will have access to fully fledged monitoring tools, reports and proactive cyber security management in order to continuously create a higher security level.
If you have previously ordered the Defender for IoT Scan from us, you will receive 20 hours of implementation free of charge for the Defender for IoT Monitoring Service.
