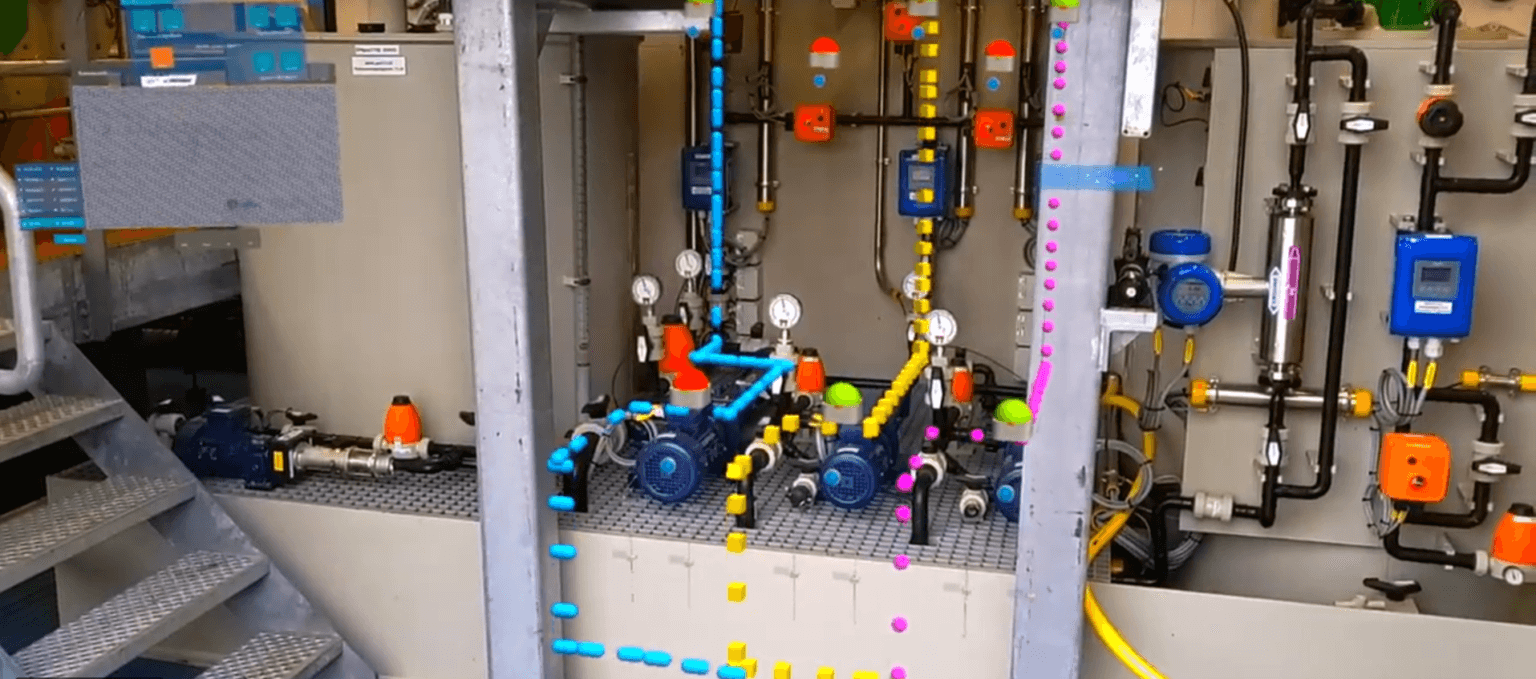
Solution
IT/OT integration in the water domain - Reduce vulnerability and risks
This so-called OT technology is known for its reliability and safety. Today, more and more IT technology is entering this domain with the aim of optimising the processes involved. But is this possible? Doesn’t this introduce vulnerabilities that previously did not exist? For instance, there is a recent example where a failure in office automation (IT) worked its way into process automation (OT), which meant that remote operation of parts of the assets ceased functioning properly. To prevent such undesirable situations, TwynstraGudde and ICT Netherlands have developed a tool to identify vulnerabilities and risks for all organisations in the water domain.
Traditionally, Operational Technology (process automation) and Information Technology (office automation) are separate worlds from an organisational and technical perspective. The introduction of IT technologies in process automation has blurred this separation. However, the associated working methods and applications differ significantly from each other, and this can create vulnerabilities that are not always taken into account. The integration of OT and IT involves an interplay of people, technology and process, and it is here that the solution is usually found.
Our tool comprises a structured approach with a concrete step-by-step plan. We can help you discover the exact location of the vulnerabilities in your organisation within a period of 12 weeks. We will give you concrete advice, which you can apply immediately to reduce these vulnerabilities. Our independent view and knowledge of the content allows us to analyse automation processes for organisations in the water domain. We do this together with our partner TwynstraGudde.
Vulnerability and risk analysis
Our vulnerability and risk analysis provides insight into vulnerabilities and risks in three pillars: OT architecture, IT/OT interdependence and cyber security. We analyse each pillar in terms of people, technology and process. This creates focus areas in which potential vulnerabilities and risks may arise. We analyse these focus areas using available documentation and interviews with relevant professionals from within the organisation. The analysis comprises relevant norms and standards such as WILMA, DAMO, IEC-62443 and the BIO.
Mirror sessions
We share our initial findings and interpretations in one or more mirror sessions. The aim of these sessions is to hold discussions in which the vulnerabilities and risks are acknowledged, clarified and complemented. We also identify and share the impact of the vulnerabilities and risks, possible causes and measures. In addition, we work together to explore what measures can be taken and which actions should be prioritised.
Immediately applicable
The vulnerability and risk analysis culminates in results and an advice that we compile in a final report. We visualise the exact areas in which the vulnerabilities and risks occur, and we provide clear advice that can be applied immediately. This is how we help organisations in the water domain to detect and remedy vulnerabilities and risks in process automation.
Are you curious about our approach? And would you like to talk to one of our consultants to discuss the possible vulnerabilities and risks in your organisation's OT? Contact Eric van der Laan, or read our experience with the Rivierenland water authority, where we investigated the vulnerability of process automation in the context of outsourcing their office automation.